Science
What is Cryptography? How Algorithms Keep Data Private and Secure
Cryptography is pivotal in ensuring information confidentiality, integrity, and authenticity in digital security. It is a fascinating field encompassing the science and art of transforming data into a secure format that authorized individuals can only understand.
In this article, we will delve into the concept of cryptography, exploring how algorithms are used to keep information secret and safe.
Understanding Cryptography
Cryptography secures information by converting it into an unreadable format, ciphertext, using mathematical algorithms. Encryption transforms plain, understandable text, known as plaintext, into ciphertext, which is essentially scrambled and unintelligible to anyone without the necessary decryption key. This encryption ensures that even if an unauthorized person gains access to the encrypted data, they cannot comprehend its meaning.
The Role of Algorithms
Algorithms form the backbone of cryptography. They are mathematical instructions that govern the encryption and decryption processes. These algorithms use complex mathematical operations to manipulate the data, making it extremely difficult to reverse-engineer the encryption without the appropriate key. There are various types of algorithms, including symmetric key algorithms, asymmetric key algorithms, and hashing algorithms, each serving different cryptographic purposes.
Symmetric Key Algorithms
Symmetric key algorithms, known as secret key algorithms, use the same key for encryption and decryption. The key, typically a string of bits, is a shared secret between the sender and the intended recipient.
The sender applies the key to encrypt the plaintext, producing the ciphertext, which can only be deciphered by the recipient who possesses the same key. Examples of symmetric key algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES).
Asymmetric Key Algorithms
Asymmetric key algorithms, also called public key algorithms, utilize a pair of mathematically related keys: public and private keys. The public key is widely distributed and accessible to anyone, while the owner keeps the private key secret.
When someone wants to send an encrypted message to a recipient, they use the recipient’s public key to encrypt the plaintext. Only the recipient, possessing the corresponding private key, can decrypt the ciphertext. Popular asymmetric key algorithms include RSA and Elliptic Curve Cryptography (ECC).
Hashing Algorithms
Hashing algorithms are cryptographic functions that take an input, such as a file or a message, and produce a fixed-size output, known as a hash value or digest. The critical characteristic of hashing algorithms is that they are one-way functions, meaning it is computationally infeasible to derive the original input from the hash value.
Hashing is commonly used to verify the integrity of data and ensure that it has not been tampered with. Well-known hashing algorithms include the Secure Hash Algorithm (SHA) and Message Digest Algorithm (MD5).
Ensuring Data Security
The strength of cryptographic systems lies in the algorithms’ complexity and the encryption keys’ length and randomness. Longer keys and more intricate algorithms make it exponentially more difficult for attackers to break the encryption and gain access to sensitive information. Additionally, cryptographic protocols and standards undergo rigorous testing and analysis by experts to identify potential vulnerabilities and ensure their robustness.
Applications of Cryptography
Cryptography finds applications in various areas, from securing communication channels to protecting stored data. It is widely used in secure internet communication protocols, such as Transport Layer Security (TLS) and Secure Shell (SSH), to encrypt data during transmission and prevent unauthorized interception. Cryptography also plays a crucial role in secure storage, such as encrypting files and folders on a computer or encrypting data on portable storage devices.
The Future of Cryptography
As technology continues to evolve, so does the field of cryptography. Quantum computing, for example, poses both opportunities and challenges for cryptographic systems.
Quantum-resistant algorithms are being developed to withstand the computing power of quantum computers, ensuring that data remains secure in the face of future advancements.
The ongoing research and innovation in cryptography aim to avoid potential threats and provide robust protection for sensitive information. In conclusion, cryptography is a vital tool in digital security.
Through the use of algorithms, it enables the transformation of data into a secure format, ensuring its confidentiality and integrity. Sens sensitive information can be protected from unauthorized access by employing symmetric key algorithms, asymmetric key algorithms, and hashing algorithms. As technology advances, cryptography evolves, adapting to new challenges and maintaining data security in an ever-changing digital landscape.
Related CTN News:
What is Data Privacy? 5 Things You Need to Know About Data Privacy

Science
NASA Switches Off Instrument On Voyager 2 Spacecraft To Save Power

NEW YORK — To save power, NASA turned off another scientific equipment on its long-running Voyager 2 spacecraft.
NASA Switches Off Instrument On the Spacecraft To Save Power
The space agency announced on Tuesday that 2’s plasma science instrument, meant to study the movement of charged atoms, was turned off in late September to allow the spacecraft to continue exploring for as long as possible, which is estimated to be into the 2030s.
NASA turned off a suite of instruments on Voyager 2 and its twin, Voyager 1, after exploring the gas giant planets in the 1980s. Both are currently in interstellar space or the region between stars. The plasma instrument on Voyager 1 stopped working years ago and was finally shut off in 2007.
The remaining four instruments on 2 will continue to collect data on magnetic fields and particles. Its mission is to investigate the regions of space beyond the sun’s protective sphere.
NASA Switches Off Instrument On Voyager 2 Spacecraft To Save Power
It launched in 1977, is the only spacecraft to have visited Uranus and Neptune. It is now more than 12 billion miles (19.31 billion kilometers) from Earth. 1 is more than 15 billion miles (24.14 billion kilometers) beyond Earth.
SOURCE | AP
Science
Hurricane Kirk Could Cause Dangerous Surf Conditions Along The US East Coast
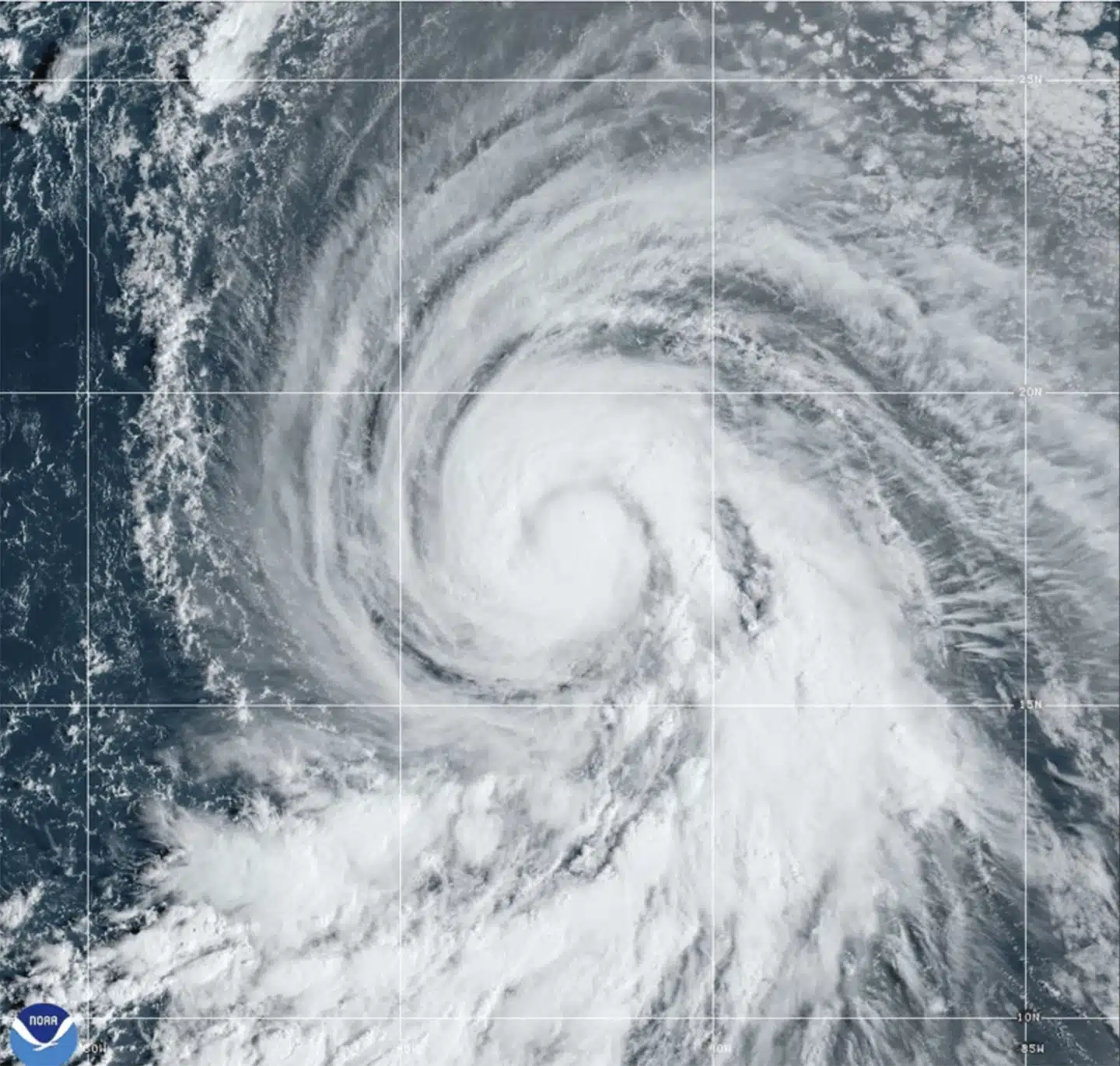
MIAMI — Hurricane Kirk’s waves could generate life-threatening surf and rip current conditions this weekend throughout the United States East Coast, as well as in Bermuda, the Greater Antilles, and the Bahamas, according to forecasters.
Kirk was a Category 3 hurricane in the middle Atlantic Ocean that might grow further but was predicted to stay away from land, according to the Miami-based National Hurricane Center on Thursday.
Hurricane Kirk Could Cause Dangerous Surf Conditions Along The US East Coast
Kirk-generated swells were forecast to reach parts of the Leeward Islands on Friday, Bermuda and the Greater Antilles on Saturday, and the East Coast and the Bahamas on Sunday, according to the center.
No coastal watches or warnings were in effect. The major storm was around 1,130 miles (1,820 kilometers) east of the Leeward Islands, with maximum sustained winds of 125 mph (205 km/h).
Meanwhile, Tropical Storm Leslie formed late Wednesday in the eastern Atlantic and is expected to strengthen into a hurricane in the following days, forecasters said. It was also not considered a threat to the land.
Hurricane Kirk Could Cause Dangerous Surf Conditions Along The US East Coast
The storm was about 540 miles (870 kilometers) southwest of Cabo Verde’s southernmost tip, with maximum sustained winds of 45 mph (75 kph), according to the center.
The storms raged in the Atlantic as rescuers in the United States Southeast sought for missing persons after Hurricane Helene struck last week, leaving a trail of death and devastation.
SOURCE | AP
Science
Giant Fossilised Footprint Of Dinosaur Found in China

(CTN News) – A team of palaeontologists believes they have discovered fossilized footprints of one of China’s largest raptors. The collection of five fossilized dinosaur footprints is half the length of a school bus.
The footprints were discovered in a dinosaur trackway in south-east China in 2020. Scientists believe dinosaurs walked over the muddy river during the Cretaceous period, leaving footprints. Some footprints have been preserved for tens of millions of years.
The dinosaur trackway was unearthed in Longxiang and is around the size of a hockey rink. Some of the footprints are unusually formed, with intact imprints of only two toes.
Fossilised footprint of megaraptor found in China

Giant fossil footprints lead to megaraptor dinosaur discovery in China
Raptors, or predatory birds, are often small and referred to as deinonychosaurs. For example, a Velociraptor is around the size of a turkey. Few raptors, such as the Utahraptor and Dakotaraptor, increased in size significantly, reaching lengths of 5 to 6 metres. The Triassic ichthyosaur was the largest raptor known until now.
According to the scientists, the predator would have attacked its prey with a pair of huge “killing claws” on each foot.
What scientists discovered recently in China is massive, far larger than the largest superpredator known to date.
Scott Persons of the College of Charleston in South Carolina, and his colleagues, added another large raptor to the list. They named it Fujianipus, and they believe it lived in East Asia some 96 million years ago.

Scott Persons at the College of Charleston in South Carolina and his colleagues added another giant raptor to the list. They named it Fujianipus, and they say it lived in East Asia about 96 million years ago. Photograph:(Twitter)
Persons and his colleagues are currently working on areas of Fujianipus’ skeleton, therefore little is known. The investigators only discovered a few of its 36-centimetre-long imprints.
“Preservation conditions were right for footprints but not so great for bones,” Persons said. However, scientists are certain that the footprints belong to a raptor because each one contains the imprint of only two toes, which corresponds to the foot anatomy of raptors. Raptors generally have three toes, but they keep one off the ground to preserve the big claw at the tip from wear and tear.
People believe Fujianipus demonstrates that raptors had the ability to grow much larger and compete with the largest predatory dinosaurs on the landscape at the time – allosauroids, some of which exceeded 10 metres or more in length.
According to Persons, raptors had an advantage over allosauroids in terms of speed. However, without fossilized leg bones, the researchers cannot correctly measure Fujianipus’ speed.
-

 News4 years ago
News4 years agoLet’s Know About Ultra High Net Worth Individual
-
Entertainment3 years ago
Mabelle Prior: The Voice of Hope, Resilience, and Diversity Inspiring Generations
-
News11 years ago
Enviromental Groups Tell Mekong Leaders Lao Dam Evaluation Process Flawed
-

 Health4 years ago
Health4 years agoHow Much Ivermectin Should You Take?
-

 Tech3 years ago
Tech3 years agoTop Forex Brokers of 2023: Reviews and Analysis for Successful Trading
-

 Lifestyles3 years ago
Lifestyles3 years agoAries Soulmate Signs
-

 Entertainment3 years ago
Entertainment3 years agoWhat Should I Do If Disney Plus Keeps Logging Me Out of TV?
-

 Health3 years ago
Health3 years agoCan I Buy Ivermectin Without A Prescription in the USA?
